Figure 3 from Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar
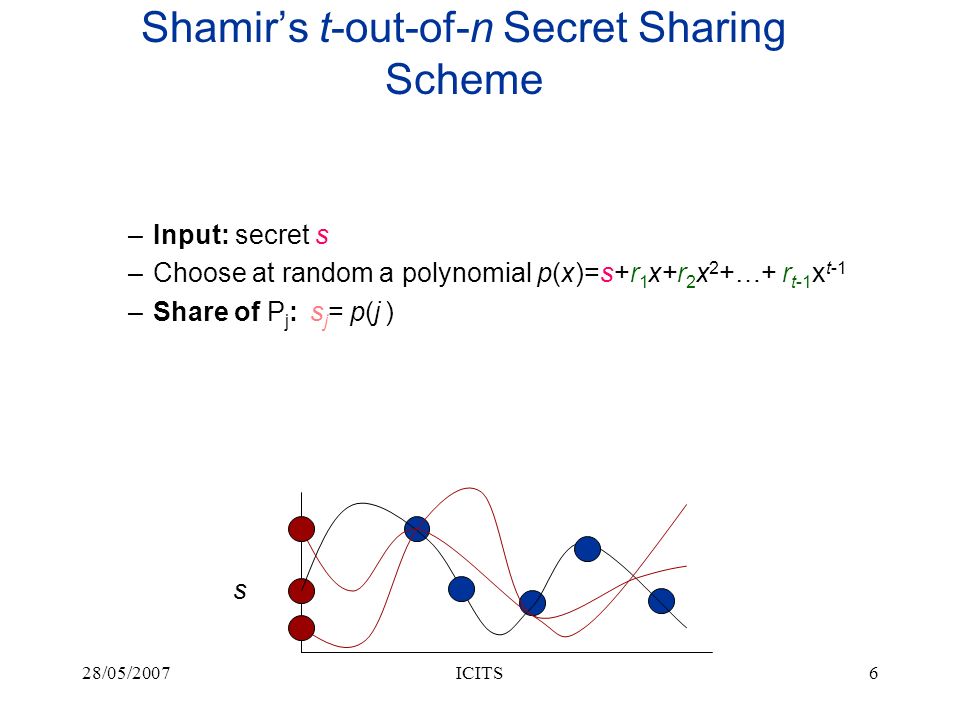
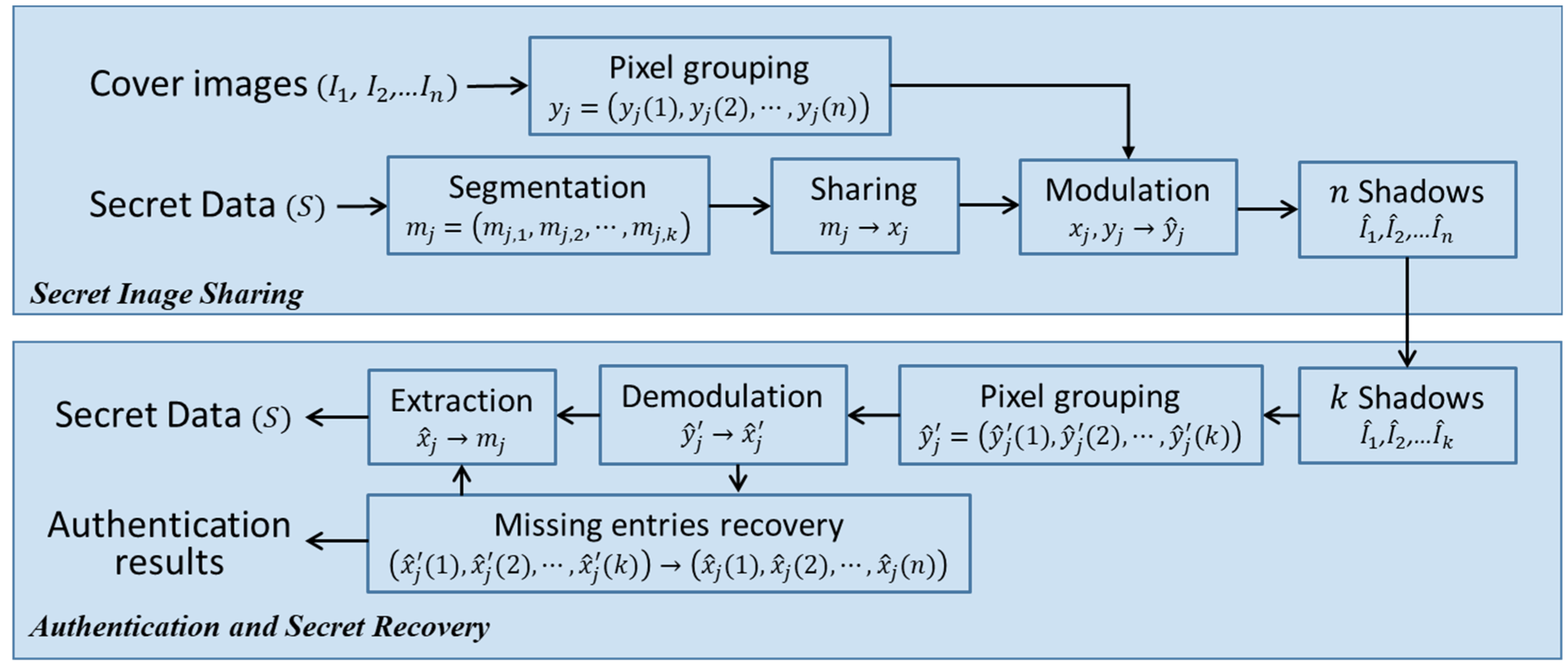
Mathematics | Free Full-Text | A k,n-Threshold Secret Image Sharing Scheme Based on a Non-Full Rank Linear Model
![PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e4fb133ee661d1d55bf333ee673c1d8e47e0bb19/12-Figure6-1.png)
PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar
![PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e4fb133ee661d1d55bf333ee673c1d8e47e0bb19/14-Figure7-1.png)
PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar
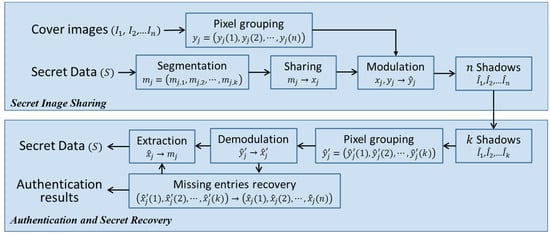
Mathematics | Free Full-Text | A k,n-Threshold Secret Image Sharing Scheme Based on a Non-Full Rank Linear Model

Is linear secret sharing over the addittive group of integers modulo $p$ with $p$ non-prime secure? - Cryptography Stack Exchange
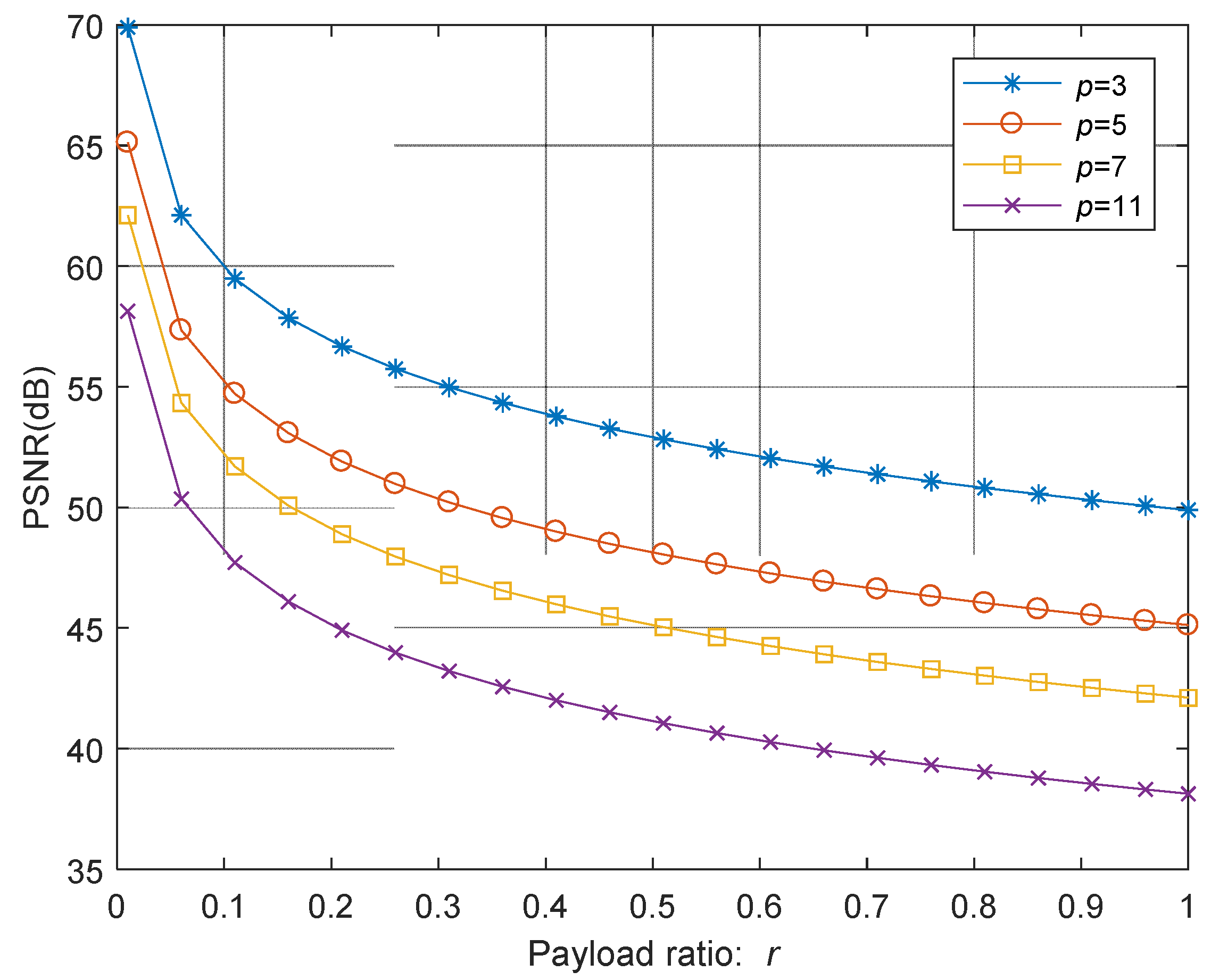
Mathematics | Free Full-Text | A k,n-Threshold Secret Image Sharing Scheme Based on a Non-Full Rank Linear Model
![PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e4fb133ee661d1d55bf333ee673c1d8e47e0bb19/3-Figure2-1.png)
PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar
![PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e4fb133ee661d1d55bf333ee673c1d8e47e0bb19/3-Figure1-1.png)
PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar
![PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar PDF] Efficient Generation of Linear Secret Sharing Scheme Matrices from Threshold Access Trees | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e4fb133ee661d1d55bf333ee673c1d8e47e0bb19/7-Figure5-1.png)
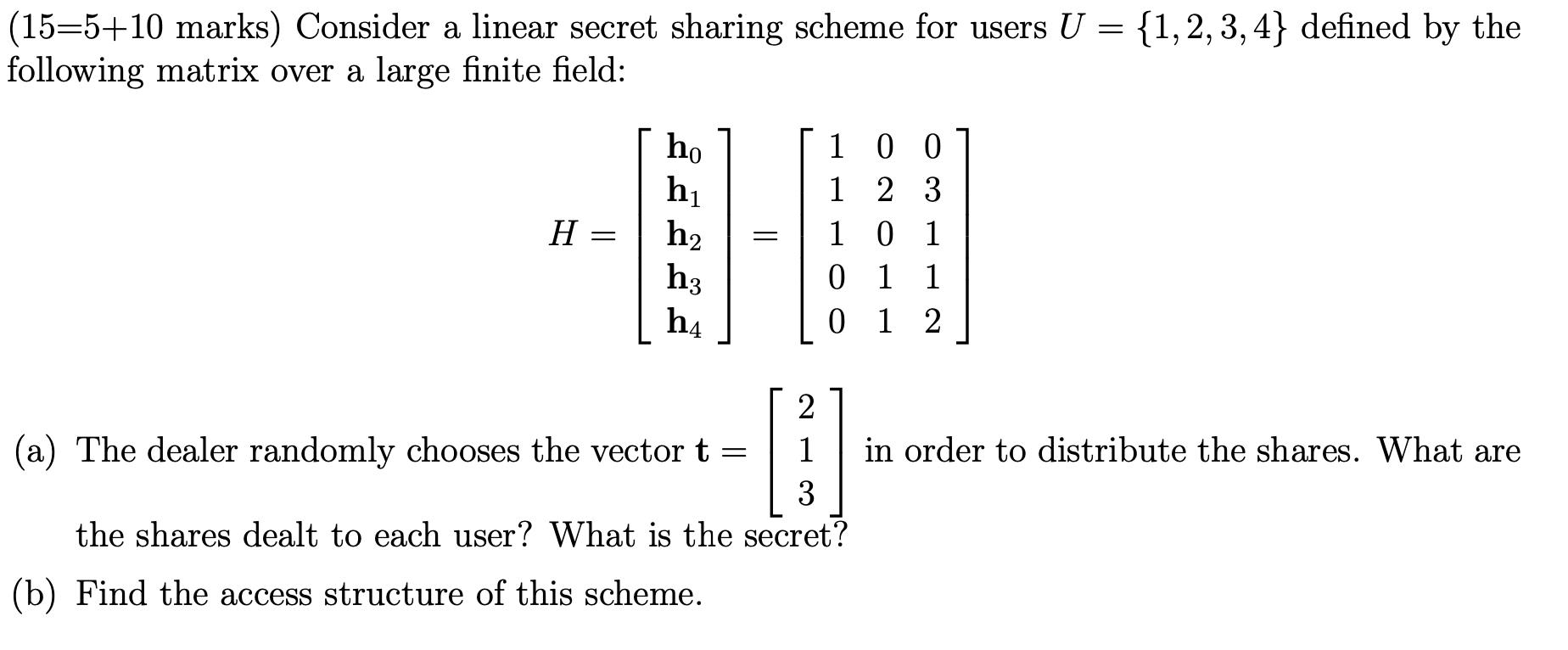

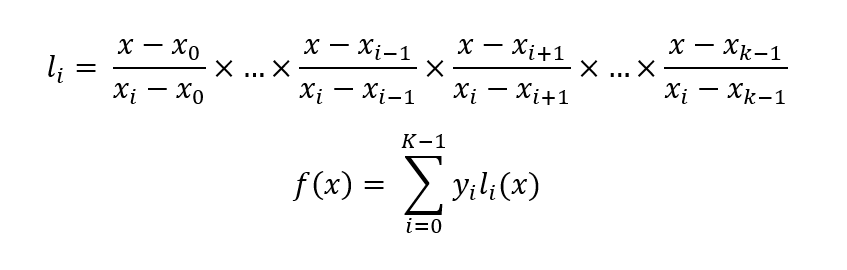


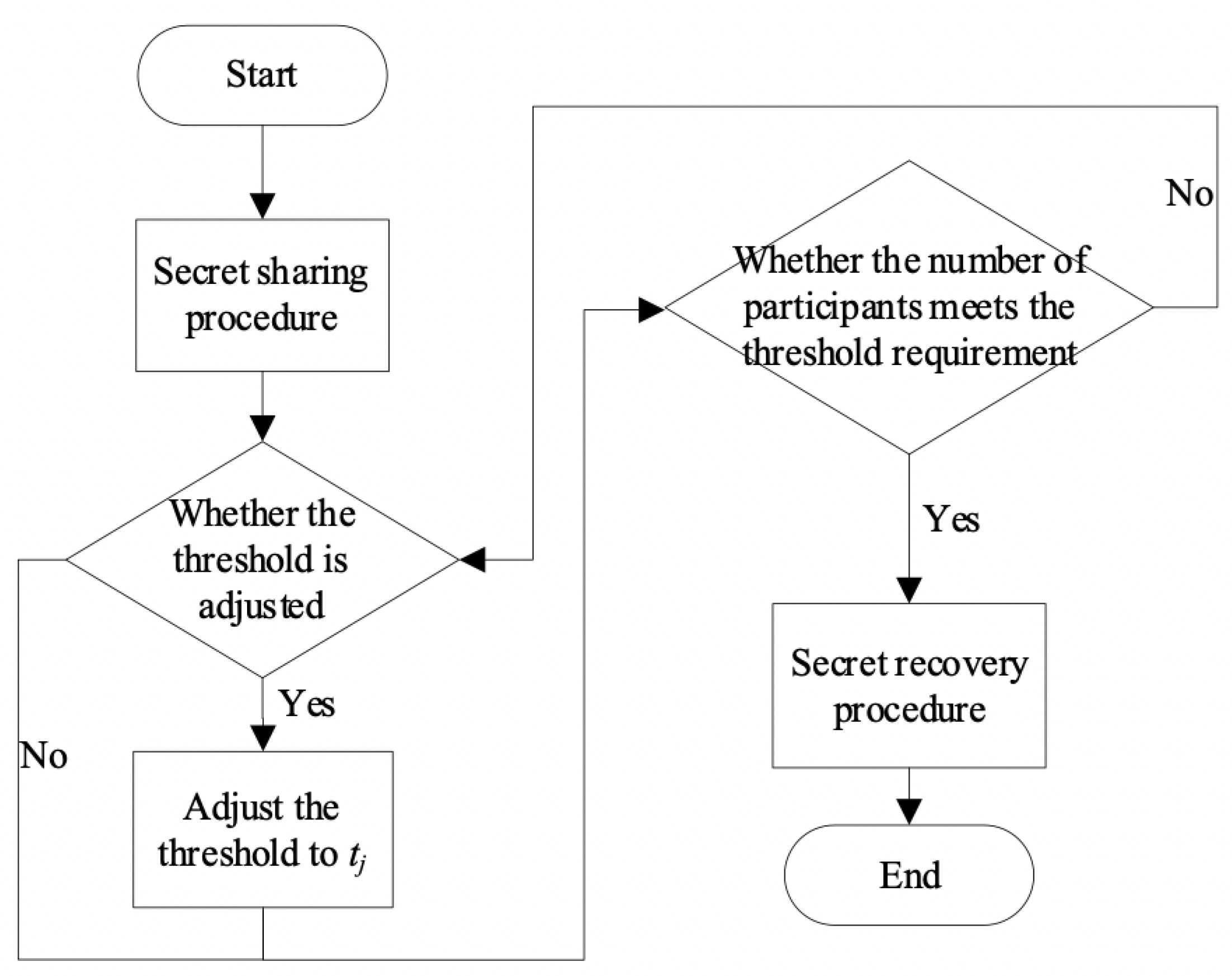



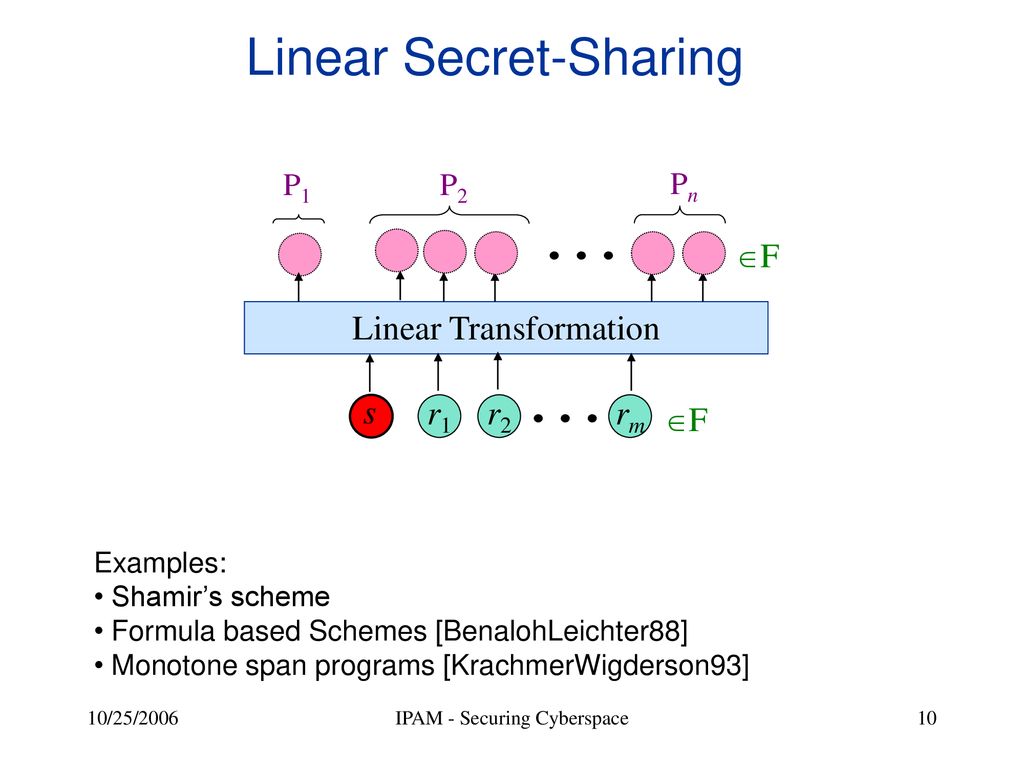

![PDF] Secret Sharing Schemes with Applications in Security Protocols | Semantic Scholar PDF] Secret Sharing Schemes with Applications in Security Protocols | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/93422b1c6e5b4b2e304e949acca06e3af2d0852f/113-FigureC.3-1.png)